What is Encryption? How it Works, Uses and Differences with Hashing
I once acquired an article that stated thatchatAre you and others protected by encryption?
Perhaps you do not actually concentrate or care in regards to the that means.
Nevertheless, it seems, this safety system is essential in order that your data can’t be learn by irresponsible third events, you understand.
On this article, Glints will clarify what encryption is, ranging from the definition, makes use of, to the kinds which can be helpful for on a regular basis web actions.
Come on, simply learn the reason under fastidiously, okay?
What are the Benefits of Learning Node.js for a Developer?
What is Encryption?
According toCloudflare, encrypt or encryption is a approach of randomizing data in order that the data can solely be learn by individuals who have entry.
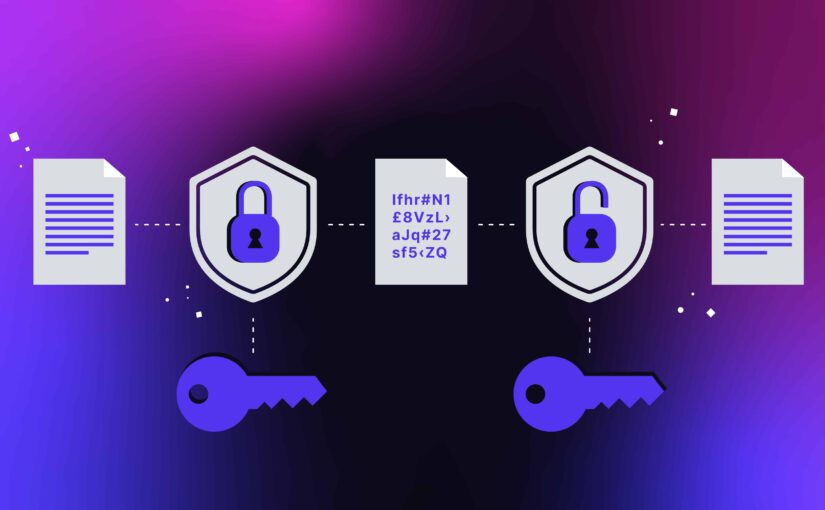
Technically,encryption is the method of changing human-readable plain text (human-readable plaintext) turns into textual content that can’t be learn and understood (incomprehensible text).
The encrypted information or text is usually known as ciphertext.
So, the objective of the method encrypt is to forestall third events from figuring out what’s being shared or mentioned.
When a 3rd celebration tries to hack, what they see is the textual content random and incomprehensible.
To have the ability to learn it, a cryptographic secret is required.
Now,cryptographic keys themselves are the characters used within the encryption algorithm to scramble textual content right into a show random and in addition in a position to change it again to type plaintext.
Though it appears to be like very random, there may be truly a sure logic system that governs the randomization.
What is Deep Learning? Definition, Types, Examples of Application and Benefits
Encryption the great ones are advanced so they don’t seem to be simply solved by simply anybody.
How Encryption Works
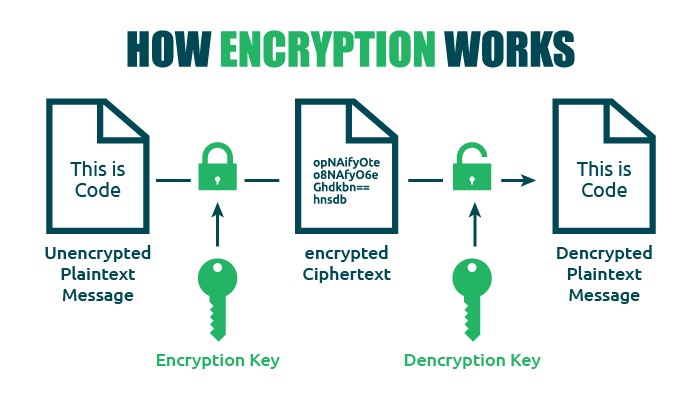
Generally, Glints has defined how encryption is completed. Effectively, truly, the method is a bit more difficult.
Earlier than Encryption to do, first it’s a must to know what cipher or a password that will likely be used to cover the unique that means of a textual content.
Then, additionally decide the variable used as the important thing.
If an encryption makes use of just one key, it’s known as a symmetric cipher.
In the meantime, if an encryption makes use of two keys which can be interconnected, it’s known as an uneven cipher.
For additional clarification, examine the reason under, come on!
1. Cipher symmetrical (symmetric cipher)
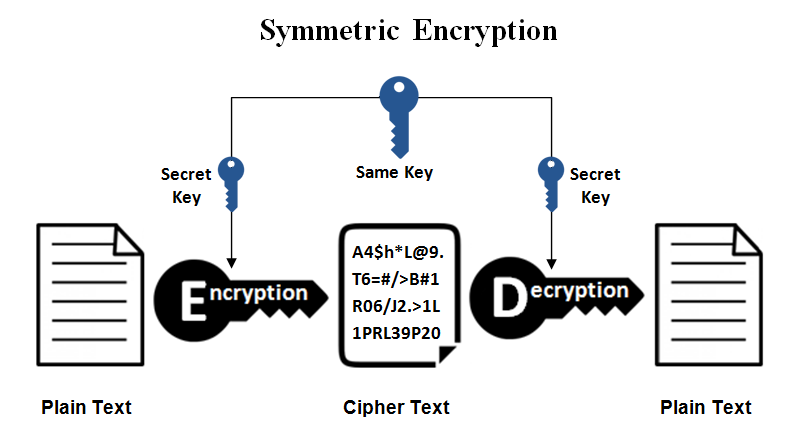
Cipher symmetric encryption is the sort that makes use of a single key.
Typically, sort cipher that is known as secret key encryption or shared secret.
For this sort, the sender or laptop system that carries out the encryption course of should share the key key with all authorities in order that the message may be decoded or decrypted.decrypt.
Sort Cipher Probably the most steadily used symmetric typecipher is Superior Encryption Commonplace (AES).
That is additionally utilized by the US authorities to guard essential confidential state info.
2. Cipher asymmetrical (asymmetric cipher)
As beforehand talked about, encryption that makes use of two interconnected keys is known as an uneven cipher.
One other identify for the sort of encryption is public key encryption.
Sometimes, these keys use prime numbers as a result of they supply stronger safety for the information being protected.
For Encryption Presently, the type of algorithm most frequently used is Rivets-Shamir-Andleman (RSA).
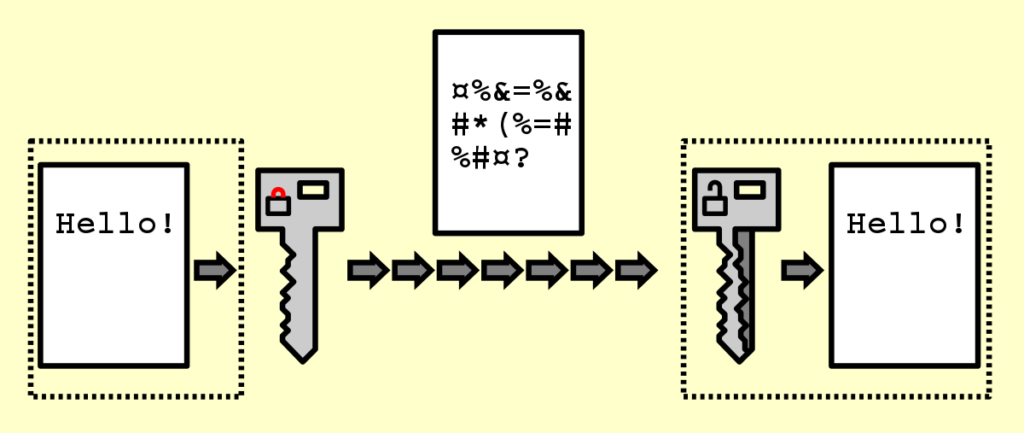
Effectively, the encryption course of with cipher is as depicted under.
Use of Encryption

As a result of Cyber security is essential, encryption is actually very a lot wanted.
Effectively, there are a number of makes use of encryption which we regularly encounter each day in accordance toLearning Hub, that’s:
1. Data encryption
Data encryption is a technique of defending info for database, information warehouses, and backup server.
For big quantities of knowledge resembling data warehouse, a job is required safety engineer and professionals in different IT fields to make sure safety utilizing technology encryption.
2. File encryption

Encryption will also be used for file.
There’s software particularly to assist keep safety file and folder on the pc or within the system cloud.
Therefore,hacker will probably be troublesome to entry your necessary information.
3. Encryption messaging
Application Messenger similar to WhatsApp, Telegram, and others often additionally use this cyber safety know-how.
The reason being, the data shared is usually susceptible to hacking.
Subsequently, encryption is a vital consideration when selecting a messenger software for day by day use, particularly for work functions.
4. Endpoint encryption

Endpoint encryption is the safety of the working system from assaults keylogger or corrupt boot information who can entry information with out permission.
That is typically wanted for laptops,server, tablets, and so forth.
Do you perceive encryption and the way necessary it’s for the safety of your information?
Principally, this know-how was created for constructive functions.
Nevertheless, generally there are difficulties or challenges that happen because of the complexity of the outline, particularly in sure conditions.
For example, as the information decryption course of turns into more and more advanced,backup data when wanted may be tougher and take a very long time.
In reality, in some circumstances, the information proprietor can not entry it resulting from sure errors.
Difference between Encryption and Hashing
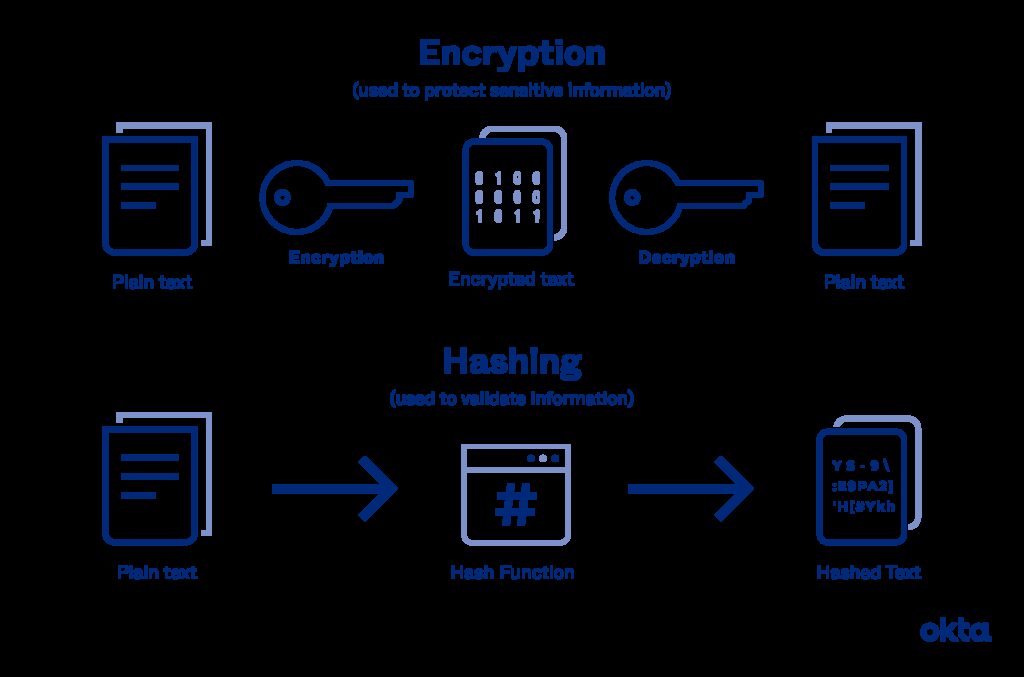
Within the discipline data safety, encryption and hashing are two practices which can be typically thought-about the identical.
In reality, in accordance toEncryption Consulting, listed here are the variations between encrypt with hashing.
1. Function
Function Encryption goes each methods, whereas,hashing stroll in a single path solely.
That’s, the outcomes of knowledge or textual content from encryption may be modified and returned once more.
In the meantime, the information or textual content that’s modified makes use ofhashing can’t be returned.
2. Types of Algorithms
The algorithms used for encryption are of two sorts,symmetric and uneven.
Whereas,hashing solely has one sort of algorithm, particularly the algorithm hashing.
3. Usage
Encryption used to guard data or textual content that’s being or has been despatched. Whereas,hashing is used to keep away from data duplication.
Encryption is usually present in functions or options chatting on social media.
However,hashing is used to guard necessary issues resembling digital signatures to passwords.
That’s some details about encryption or encrypt. Briefly,encryption ensures that your information or textual content is saved safely from hackers.
The ensuing encrypted data or text is known as ciphertext which can’t be solved and not using a cryptographic key.
Well, aside from details about encryption, you may also discover out extra about info and technology by reading varied IT articles on the Glints Blog