5 Best Cloud Security Tips Every Organization Should Follow

When running a company or organization, it is crucial for you to pay attention to cloud computing safety. Cloud safety is a set of procedures and applied sciences meant to make sure that knowledge, purposes, and infrastructure saved within the cloud are safe.
Within the midst of the event of cloud utilization which is changing on-premise storage. Together with the advantages, data security risks should even be thought of severely.
Subsequently, it is crucial for corporations or organizations to know some attention-grabbing cloud safety ideas that may be carried out as a safety measure if sooner or later there’s a knowledge disruption or catastrophe.
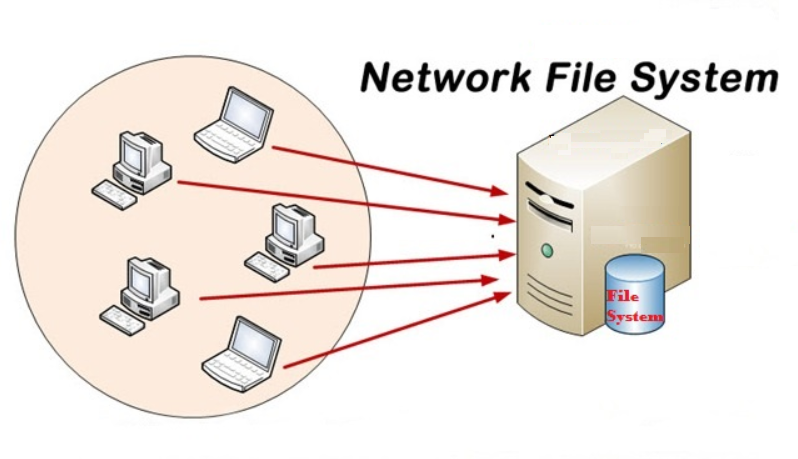
What is Network File System (NFS)? Defenition, How It’s Work and Beneftis
Listed below are 5 steps you may take to take care of data security.
1. Staff Training on Awareness of the Significance of Sustaining Cloud Security

Offering an understanding of cloud security for all employees in a corporation or firm is important to shut safety gaps as a lot as attainable. As a result of principally, potential risks that assault techniques or data may occur to anybody in sure conditions.
Coaching practices involving firm or organization staff will focus on primary cloud safety ideas, potential safety threats, and greatest practices in securing knowledge and entry to cloud techniques.
This exercise goals to make employees conscious of the security dangers which will happen if safety practices are usually not applied correctly. It additionally consists of an understanding of how safety incidents can negatively affect an organization.
Employees are taught how they will play a task in holding the cloud safe, corresponding to utilizing robust passwords, not clicking on suspicious hyperlinks or attachments in emails, and reporting suspicious exercise or safety incidents to the IT or safety division.
Moreover, staff are additionally knowledgeable about safety insurance policies to comply with, corresponding to robust password insurance policies, entry guidelines, and actions to soak up emergency conditions.
2. Use Strong Encryption for Cloud Security

Encryption is the method of converting data right into a format that can not be learn with out the suitable encryption key. Within the context of cloud storage, there are two forms of encryption which might be generally used, specifically data in transit and data at relaxation.
Data in transit encryption is data that’s encrypted whereas it is being transmitted over a network. For instance, solely after we entry cloud purposes or send data through the web. This prevents unauthorized events from having the ability to entry or perceive the information whereas in transit.
Second, encryptiondata at relaxation which implies the data is encrypted whereas it’s saved on the cloud supplier’s servers. Even when somebody manages to entry the bodily server, the information will stay protected as a result of it can’t be learn with out the proper encryption key.
Using encryption is necessary to offer an extra layer of safety in opposition to theft or unauthorized entry to data.
Cloud Object Storage: Solutions to Overcapacity
3. Multi-Issue Authentication (MFA) to Maintain Cloud Security

Multi-factor authentication is an extra step past getting into a password that’s required to entry an account or cloud system. It goals to extend safety by including an extra layer of authentication.
The way in which MFA works is to enter your account or system password, then wait for extra authentication within the type of a code despatched via SMS, authentication software, or verification of a bodily code corresponding to a particular token. As soon as profitable, you may be given entry to your account or cloud system.
MFA makes it tough for unauthorized events to entry your account, even when they’ve the password. It is because in addition they need to have entry to a second authentication technique that solely the account proprietor has.
By combining data encryption and MFA, corporations or organizations can considerably enhance their cloud safety.
4. Active and Responsive Cloud Security Monitoring

One of the important ideas for sustaining cloud safety is to hold out lively and responsive safety monitoring. Active safety monitoring is monitoring and monitoring of the cloud surroundings periodically to detect suspicious or unusual exercise.
On this case, automated monitoring instruments are wanted that scan logs and operational knowledge for indicators of potential safety threats. Energetic monitoring permits organizations to establish safety incidents as quickly as they happen, which might cut back their affect.
In the meantime, responsive safety monitoring is motion taken after the detection of a risk or incident. As soon as suspicious exercise is detected, response steps should be taken instantly.
Issues to do embrace isolating infected techniques, stopping unauthorized entry, accumulating digital proof, and growing a plan to handle incidents.
The significance of lively and responsive cloud safety monitoring is that you could perform early detection of potential threats and supply a fast response for responsive incident decision. Other than that, you can even make sure the safety of delicate knowledge from injury or risk of assault.
5. Select a Trusted Cloud Security Service Provider

Lastly, what it’s worthwhile to keep in mind and think about as quickly as attainable is selecting a reliable cloud service supplier. Selecting a reliable supplier has a significant affect on the safety and privacy of information saved within the cloud.
You may choosetrusted cloud service supplier considering that the corporate has a powerful repute for safety, privateness and compliance. They often meet sure security requirements and have certifications that adjust to relevant trade or rules.
Under are several causes it’s best to know earlier than making a selection on a cloud service supplier.
- Strong security
Trusted cloud service providers will spend money on their safety infrastructure assets. Other than that, in addition they positively have a devoted staff of safety specialists who constantly monitor and handle potential threats.
- Compliance with regulations
A trusted cloud service supplier will all the time adjust to the safety necessities set by rules. It is a assure to offer confidence that your knowledge is protected and managed based on relevant insurance policies.
- Reliable support and service
Good help providers and technical help in resolving safety points will likely be offered as a part of the corporate’s repute. This will likely be done if a safety incident happens or if the group requires help with safety configuration.
- Availability and performance of cloud services
A trusted cloud service supplier should have robust and dependable infrastructure, in order that it may assure the supply and performance of cloud providers to make sure easy operations.
- Transparency regarding disturbances that happen in data
You’ll always get safety experiences and transparency about safety incidents they’ve dealt with. On this case, organizations or corporations also can higher perceive and handle safety dangers.
By considering these 5 aspects in selecting a trusted cloud service supplier, you additionally want to pay attention to the corporate’s repute and the staff of experts they’ve.
On this case, safety servicesDCloud might help you determine what kind of security services are wanted to guard the techniques and data of your group or firm.